I read a lot of news from the 20 min online website using the 20 min online .ch app for iOS. Every now and then, people start commenting the articles (and leave behind a lot of silly comments). My goal was to get the URL where this data (the comments) is loaded from (for some unexplainable reasons :-)). As the website offers the articles as RSS feeds, the assumption was that the app will load the comments also via RSS feed.
So how to eavesdrop the network traffic between the iPhone and the Internet? The iPhone has four communication interfaces: GSM, WLAN, Bluetooth and USB (neglecting all non-networking interfaces like display, speaker, etc.). Now there must be way to eavesdrop on one of those. The WLAN was the obvious choice. Either your local router supports very detailed logging or you need to set up your computer as router and inspect the packets transferred with wireshark. So here I write about how to setup your computer as router.
1. start the linux os of your choice
In a recent version of Ubuntu, you have the ability to create a wireless network managed by your computer out of the box.
2. create a new (infrastructure mode) WLAN
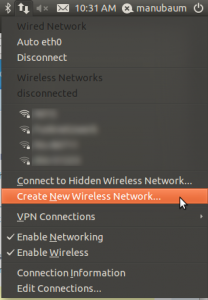
3. name it however you want, for simplicity security is omited
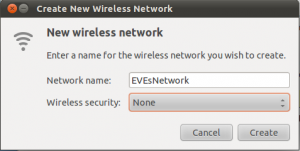
4. get your iPhone/iPad and put it into airplane mode
Then inside the the Wi-Fi menu, switch on Wi-Fi and select the newly created WLAN (yes, we are still in airplane-mode). This forces the iPhone to route all packets through our WLAN network / we assure no data is sent using GSM.
5. start wireshark as admin (in a console run: sudo wireshark &)
Click on Capture ->; Interfaces and chose the WLAN device that communicates with the iPhone (most likely wlan0). Now, you capture all network traffic between the iPhone and the Internet.
6. start the app on the iPhone/iPad that you want to inspect
In this example, I analyzed the Facebook app for iOS. The question is, where the image data is fetched from.
As a HTTP request will do a at least an SYN, SYN-ACK, ACK for connection establishment (and further stuff) you best set the filter in Wireshark to “HTTP”. Then you only see the actual GET requests from the client and the responses from the server.
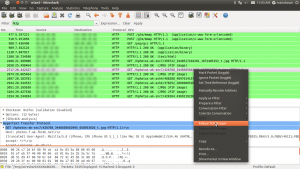
Right click a packet and chose “Follow TCP stream”:
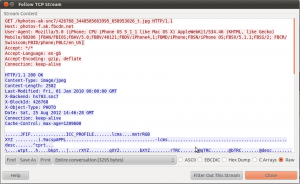
Et voilà, we now know where the app is loading its data from:
Host: photos-f.ak.fbcdn.net (where fbcdn is most likely standing for Face Book Content Delivery Network)
GET parameter: /hphotos-ak-snc7/426768_3448505663995_658953026_t.jpg
Combining it, we end up with the following URL:
http://photos-f.ak.fbcdn.net/hphotos-ak-snc7/426768_3448505663995_658953026_t.jpg
In case SSL is used, you wont see any packets when filtering for HTTP. This means you cannot inspect any packet when the app uses SSL (meaning https instead of http), which is the very purpose of this encryption protocol.